After you've set up LANDesk 802.1X NAC support in your environment, you can perform these compliance security management tasks.
NOTE: Additional
servers required for LANDesk 802.1X NAC
For Network Access Control you should have already set up a
remediation server and configured (or added) it in the console. For
802.1X NAC, you should also have an 802.1X Radius server. For more
information, respectively, see Setting up and configuring a remediation server, and
Setting up a 802.1X Radius server
or proxy.
Read this section to learn about:
To learn more about compliance scanning and other NAC management tasks such as updating compliance security rules and policies on posture validation servers, updating remediation resources on remediation servers, adding unmanaged devices to the Unmanaged Device Discovery tool, viewing affected devices, and configuring logging, see Managing 802.1X NAC compliance security.
Compliance security criteria is defined by the following factors:
See the appropriate procedures below for each of these tasks. See Using the Compliance group to define a compliance security policy, and Publishing NAC settings.
You must have a LANDesk Security Suite content subscription in order to download the various types of security content, such as application and operating system vulnerability definitions (and required patches), spyware definitions, blocked application definitions, virus definitions, system configuration security threat definitions, and so on.
Without a Security Suite license, you can't access the Security services, and can't define compliance security using those security definitions.
Use the Patch and Compliance tool to download different security type definitions, such as vulnerability, spyware, antivirus, and security threat definitions. For more information on using the Patch and Compliance download features, see Downloading security content.
As explained above, the contents of the Compliance group determine your baseline compliance security policy. You can have minimal compliance security made up of just a few vulnerability and security threat definitions, or you can create a complex, strict security policy that is comprised of several security definitions. You can also modify the compliance security policy at any time simply by adding and removing definitions from the Compliance group.
NOTE: Patch and
Compliance right required
Only an administrator or a user with the Patch and Compliance right
can add or remove definitions to and from the Compliance group.
The following security content types can be added to the Compliance group to define a compliance security policy:
NOTE: You can't add blocked application definitions to the Compliance group to define compliance security policies.

Publishing NAC settings sends information and resources to posture validation servers and remediation servers that is required in order to implement the posture validation process and enforce compliance security.
In order to publish NAC settings from the console, you must have at least one remediation server, and user credentials configured.
NOTE: The initial
publish must include all settings
The first time you publish NAC settings to your posture validation
servers and remediation servers, you must include all of the
NAC settings, including NAC content and infrastructure files (see
below for details about these files). Subsequent publishing can
include NAC content or compliance rules only. Typically, the
infrastructure files only need to be published once to remediation
servers.
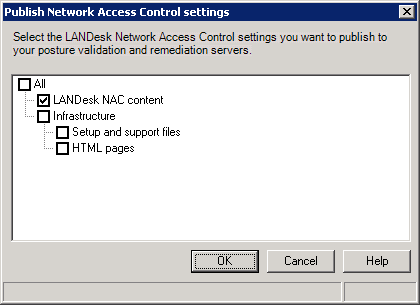
Use this dialog box to publish NAC settings to posture validation servers, and to publish remediation settings (resources) to remediation servers on your network.
The NAC remediation pages are HTML files that are published to remediation servers with the Publish NAC settings tool in the console. These remediation pages are part of the remediation infrastructure files. Typically, these files only need to be published once to remediation servers.
The HTML files are located in the following folder on the core server:
ManagementSuite\Install\TrustedAccess\RemediationServer
The HTML pages are merely templates, and you should modify them to suit your own compliance security needs and requirements. For information on how to customize the HTML pages, see Customizing the remediation pages.
The sections below describe the purpose of each HTML page.
This HTML page is used to inform the corporate end user of a connecting device that the device posture has been evaluated and is determined to be healthy, according to the compliance security credentials, and that it has been granted full access to the corporate network.
The name of this HTML page is: Healthy.html
The healthy status page will only be seen when a device transitions from unhealthy to healthy. It will not display each time a device postures as healthy.
The URL to this page on the remediation server should be entered in the Healthy URL field when you configure the remediation server.
This HTML page is used to inform a visitor to your corporate network that you have implemented compliance or network access control security on your network and that they can choose to either browse the Web (Internet access only) or have their computer scanned for vulnerabilities or other security risks, and remediated if necessary, before being allowed access to the corporate network. Links are provided on this HTML page that allow Internet access only or that allow the visitor to download and install the necessary software for compliance scanning and remediation so that their device can be have full access to the network.
The name of this page is: Visitor.html
This page provides links that lets the user either be granted Internet access only, or lets them download and install the trust agent and necessary software for remediation so that their device can be repaired, rescanned, and allowed full access to the network.
The URL to this page on the remediation server should be entered in the First time visitor's URL field when you configure the remediation server.
This HTML page is used to inform the end user of the connecting device that their device has been scanned and does not meet one or more of the compliance security credentials, is considered unhealthy, and has been denied access to the network. The network administrator should customize this HTML page so that it can show which vulnerabilities or other security exposures were detected on the device, and provide specific instructions on how to remediate them. Once the device is repaired, the end user must log into the network again to be allowed access.
The name of this page is: FailedEmployee.html
The URL to this page on the remediation server should be entered in the Employee's failed to connect URL field when you configure the remediation server.
This page is used to inform a visitor to your corporate network that their device has been scanned and does not meet one or more of the compliance security credentials, and has been denied access to the network. As with the unhealthy employee status page, network administrators can customize this HTML page so that it can show which vulnerabilities or other security exposures were detected on the device, and provide specific instructions on how to remediate them. Once the device is repaired, the visitor should click the Security scan for network access icon that now appears on their desktop.
The name of this page is: FailedVisitor.html
The URL to this page on the remediation server should be entered in the Visitor's failed to connect URL field when you configure the remediation server.
As mentioned previously, the HTML remediation pages are merely templates that you can manually edit and modify to suit your specific compliance security requirements and policies.
You can use any HTML editor to modify the HTML files. You can modify the existing text to provide additional helpful information specific to your corporate network, and add HTML DIV sections for the security definitions that are included in your compliance security policy (i.e., the definitions contained in the Compliance group in the Patch and Compliance tool).
Keep in mind that if you change an HTML file on the core server after it has been published to remediation servers, you must republish the files to the remediation servers before they can be presented to connecting devices (select HTML pages under the Infrastructure group on the Publish NAC Settings dialog box).
It can be especially useful for corporate end users as well as visitors to your network if you customize the "failed" (or unhealthy) pages so that they can see exactly what the security problems are with their computer and what specific steps need to be taken in order to remediate the problem so their device can be rescanned, evaluated as healthy, and allowed full access to the network.
These pages are designed to dynamically display content when a detected vulnerability can't be repaired by the security scanner's remediation tool. In other words, if the end user device is scanned and vulnerabilities or other security exposures are detected (such as system configuration security threats, spyware, etc.), and the repair job fails, the failed (or unhealthy) HTML page can show those specific security definitions identified by their unique ID number along with other additional information that instruct the end user how to remediate the problem as long as the system administrator has added a DIV section for that security definition (see a DIV section example below). If remediation fails for a security definition, and that definition does not have a corresponding DIV section in the HTML file, no information specific to that definition will display in the end user device's browser.
Below is an example of text that would appear in the browser if a device failed the compliance security scan and was determined to be unhealthy. This example is based on the boilerplate text already in the failed HTML files, and describes two security definitions that could not be remediated:
| Automatic Windows Update (ST000003): | |
|---|---|
| Step 1: Click on Start | |
| Step 2: Click on Control Panel | |
| Step 3: Open Automatic Updates | |
| Step 4: Click on Automatic | |
| Step 5: Click OK | |
| No Antivirus Software (AV-100): Click here to install the Symantec Anti-Virus Client |
And here is the actual HTML code for that example:
<div style="display:block;clear:both;"> </div>
<div id="ttip">
<p>
<ul>
<li>Step 1: Click on Start</li>
<li>Step 2: Click on Control Panel</li>
<li>Step 3: Open Automatic Updates</li>
<li>Step 4: Click on Automatic</li>
<li>Step 5: Click OK</li>
</ul>
</p>
</div>
<div id="ttip">
<p>
<strong>No Antivirus Software (AV-100):</strong> <a href="symantec.exe"><strong>Click here</strong></a> to install the Symantec Anti-Virus Client
</p>
</div>
The security definition is identified by the following code in the HTML file:
<div id="ttip">
Where "ttip" is the actual ID of the security definition. You can find a definition's ID on its properties page in Patch and Compliance. Type the ID exactly as it appears in the definition's properties.
If that particular security definition's remediation fails, the contents of the DIV section will dynamically appear in the end user browser and provide the end user with useful information to remediate the problem (to the extent that you've entered that information).