This section describes how to plan, set up, configure, and enable LANDesk 802.1X NAC support in an existing NAC environment.
The LANDesk 802.1X NAC tool is designed to support and extend the security of an existing 802.1X Radius server implementation on your network. LANDesk 802.1X NAC support adds authentication and compliance capabilities to basic 802.1X access control functionality.
IMPORTANT:
Technical knowledge and expertise required for setting up
NAC
Note that NAC requires additional hardware and software
configuration beyond the basic core server installation. Because of
the technical nature of this additional setup work, this guide
assumes you are familiar with 802.1X Radius server configuration,
802.1X authentication and health posture validation, and advanced
networking infrastructure design principles and administration.
Read this section to learn about:
After you've completed the setup tasks for LANDesk 802.1X NAC support, the next step in implementing NAC is to define your compliance security policy, publish NAC settings to the appropriate servers, and customize the HTML remediation pages as desired. For information on performing these tasks, see Defining compliance security criteria and publishing NAC settings.
Other ongoing NAC management tasks include: ensuring 802.1X NAC services is enabled, using the allow/restrict access to everyone option, understanding what happens when connecting devices are postured, updating compliance security rules and policies and republishing NAC settings, adding unmanaged devices to the Unmanaged Device Discovery tool, viewing affected devices, and configuring logging. For more information, see Managing 802.1X NAC compliance security.
For your convenience, use this task checklist to help keep track of the steps required to set up LANDesk 802.1X NAC. See the Quickstart task list for LANDesk 802.1X NAC.
802.1X is a IEEE security protocol used for port-based network access control. 802.1X provides authentication to devices by either establishing a connection or preventing access if authentication fails. 802.1X is based on EAP (Extensible Authentication Protocol), and most recently PEAP (Protected Extensible Authentication Protocol). 802.1X is supported by most network switches, and can be configured to authenticate clients that have agent software installed.
802.1X NAC is a Radius proxy authentication and network access technology that works with all major switching vendors supporting the 802.1X standard. With 802.1X NAC, a Radius server (either a Microsoft IAS server with the EAP IAS plug-in, or a Radius server with the 802.1X proxy) performs posture validation, or in other words checks for security policy compliance.
Standard 802.1X authentication requires a user name and password in order to access the network. LANDesk 802.1X NAC extends this basic model by also requiring that the standard LANDesk agent (CBA) is installed on managed devices requesting network access, and the supplicant device is determined to be compliant with your custom security policy. NAC verifies the presence of the agent (CBA) by looking for a unique device ID created by the agent itself. (Note: The EAP will not try to authenticate unless it can find the device ID.)
802.1X NAC with the EAP IAS plug-in uses a proprietary NAC EAP agent that resides on both the IAS Radius server and on managed devices. The LTA EAP agent is installed on your managed devices via an agent configuration.
In addition to the specific 802.1X Radius server component, and required switch and router configuration, you must also set up a remediation server in order to implement Network Access Control.
With 802.1X NAC, the Radius server acts as the network access decision point and works in conjunction with the network switch. The switch acts as the network access control device and forwards device authentication requests to the Radius server which performs the actual authentication. Depending on the results that are returned to the switch from the Radius server, the switch allows or denies device access to the network.
This section describes the components that comprise 802.1X NAC. Additionally, this section describes what happens when a device attempts to access or connect to the corporate network when NAC is enabled.
The following components are required for LANDesk 802.1X NAC.
| Component | Description |
|---|---|
|
Core server |
Provides the Patch and Compliance tool used to: Download security content (such as OS and application vulnerability definitions, spyware definitions, etc.) Define compliance criteria Configure remediation servers Configure Radius proxy installation (MSI) packages Configure and publish NAC settings (including compliance security policies and remediation resources for scanning and repairing devices) |
|
Radius server plug-in, Or Radius proxy |
Acts as the network access decision point. Use the 802.1X IAS server plug-in if you want to utilize an existing IAS server (or configure a new IAS server). Use the Radius proxy method if you have a Radius server other than IAS, or if you want to use PEAP as the specified EAP type. |
|
Remediation server |
Contains the necessary setup and support files (security type definitions and required patches, as well as the HTML remediation pages used to scan devices for vulnerabilities) identified by your security policy. Remediates any detected vulnerabilities so that the device can be scanned as healthy or compliant and access the network. |
|
Switch |
Acts as the network access control device and forwards device authentication requests to the Radius server, which performs the actual authentication. |
|
Router |
Acts as a network access device that enforces the compliance security policy. Communicates with both the connecting device attempting access and the 802.1X Radius server to evaluate the posture credentials of the endpoint device. In other words, in a 802.1X NAC environment the router is the policy enforcement point on the network and grants or denies access privileges. |
|
Devices |
User devices, attempting to access your corporate network. Typical endpoint devices include desktop computers and laptops but may also be clientless devices such as printers. NAC allows you to evaluate the health status of these connecting devices and restrict network access based on their posture credentials. |
The workflow below describes the communication flow between the various components in a 802.1X NAC environment when the device attempting to access the network has the LANDesk 802.1X agent installed.
NOTE: Compliance
security scans
With the Patch and Compliance tool you can create and configure a
compliance-specific security scan that checks target devices for
compliance with your customized security policy. A compliance scan
is based on the contents of the Compliance group and can be run as
a scheduled task or as a policy. For information on updating
compliance security rules and policies and republishing NAC
settings, see Managing 802.1X NAC compliance
security.
You should keep the following issues in mind when implementing LANDesk 802.1X NAC support in an existing 802.1X Radius server environment.
You need to set up and configure a remediation server only if you've selected to use a DHCP quarantine network instead of the TCP/IP self-assigned IP address method to quarantine unhealthy devices. 802.1X NAC with self-assigned IP addressing uses the built-in NIC TCP/IP functionality.
For more information and step-by-step instructions, see Setting up and configuring a remediation server.
As stated previously, LANDesk 802.1X NAC enhances an existing 802.1X NAC environment by adding authentication and compliance functionality. LANDesk 802.1X NAC requires an 802.1X Radius server or Radius proxy.
Choose one of the following methods to implement LANDesk 802.1X NAC.
NOTE: Use the IAS Radius server plug-in if you specify the EAP type MD5. Use the Radius proxy if you specify the EAP type PEAP. (You can also use the Radius proxy if you have a Radius server other than IAS.)
The sections below provide step-by-step instructions for both configurations.
NOTE: Switch and
router configuration
After you set up the Radius server, you must also configure your
network switch and router for LANDesk 802.1X NAC. Because switch
and router hardware is unique to each network environment, specific
instructions for every type of hardware can't be provided here.
When configuring your switch and router for 802.1X NAC, follow the
basic guidelines for functionality and topology requirements
described in the Understanding the 802.1X NAC
components and process and Network topology and design considerations sections
above. Also, you can go to the LANDesk Support site for switch and
router configuration recommendations and sample configuration
files.
Use the 802.1X IAS server plug-in if you want to utilize an existing IAS server (or configure a new IAS server) for 802.1X authentication.
The steps below describe how to install (if necessary) and configure an IAS server with the EAP plug-in. Complete all of the steps before enabling 802.1X NAC in the console.
NOTE: You can verify this new EAP type in the Remote Server Properties page. To do this, go to Control Panel > Administrative Tools > Routing and Remote Access. Right-click the remote server, click Properties, click the Security tab, click Authentication Methods, and then click EAP Methods. The LTA EAP type should appear in the methods list. If LTA EAP isn't in the list, you need to install it from the core server.
You need to configure a remote access policy that uses the EAP method for authentication.
You can do this in either the IAS tool, or in the Routing and Remote Access tool.
Now you need to add the network switches (as Radius clients) that you want to use with 802.1X authentication.
You perform this task in the IAS tool (IAS > Radius Clients).
By adding a switch as a Radius client, the Radius server is able to recognize and process authentication requests through that switch.
You must now create a new user on the Radius server in order to establish login credentials. This user's user name and password will determine the authentication credentials for managed devices configured with 802.1X NAC that attempt to access the network.
Use the server's Computer Management tool to perform this task.
- Clear the User must change password check box
- Select the User cannot change password check box
- Select the Password never expires check box
- Make sure the Account is disabled check box is clear
The user name and password entered here are the login credentials that an end user must provide in order to respond successfully to the authentication identify request during the 802.1X authentication process. Then, the credentials are sent to the Radius server, along with the device EAP data, in order to determine whether the device is granted access to the network.
You can also enable 802.1X NAC in the console. (The other method of implementing 802.1X NAC is to configure and install a Radius proxy. For more information, see Using the Radius proxy (for PEAP).)
After you've completed all of the setup tasks noted above, you can now enable LANDesk 802.1X NAC.
You do this from the console (Tools > Security > Network Access Control).
This essentially turns on 802.1X authentication services on your network. However, you must still configure managed devices with the 802.1X agent before their network access can be managed and enforced through 802.1X authentication. See Deploying the LANDesk 802.1X NAC agent to managed devices.
The next section describes how to configure LANDesk 802.1X NAC using the Radius proxy method.
Use the Radius proxy if you want to utilize the EAP type PEAP. (You can also use the Radius proxy if you have a Radius server other than IAS.)
The 802.1X Radius proxy can be installed on the following types of Radius servers:
NOTE: Coexisting
with Radius server software
The 802.1X Radius proxy can coexist on servers running Radius
server software. If your Radius server is hardware-based, you
should install the 802.1X Radius proxy on a separate server.
The Radius proxy communicates between the switch and the device with the 802.1X agent installed. The proxy is in the middle: the device authenticates with the Radius proxy and the proxy passes the ID and password on to the Radius server. If the agent is not installed on the device attempting to make a connection, then the Radius proxy denies access.
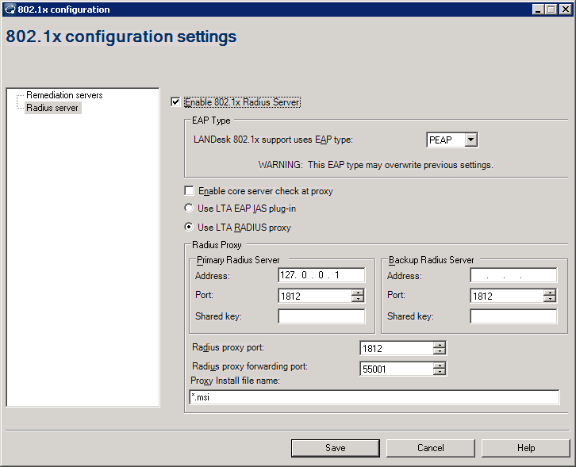
In order to use the Radius proxy, you must enable LANDesk 802.1X NAC, configure the settings for a Radius proxy installation file, and install the Radius proxy on your Radius server.
You do this from the console (Tools > Security > Network Access Control).
This essentially turns on 802.1X authentication services on your network. However, you must still configure managed devices with the 802.1X agent before their network access can be managed and enforced through 802.1X authentication. See Deploying the LANDesk 802.1X NAC agent to managed devices.

The Radius proxy installation adds data (such as address and port information) to the server registry.
NOTE: Not
supported on 64-bit platforms
Do not install the Radius proxy on Windows 98, or on any
64-bit platform.
The section below describes the dialog boxes referenced in the tasks above.
Use this dialog box to select a remediation server and publish network access control settings to the remediation server, and to enable 802.1X NAC on your network.
If you're using the IAS Radius server plug-in, you simply enable the Radius server and specify the EAP type (MD5), and then select the IAS plug-in option.
If you're using the Radius proxy, you must not only enable the Radius server and specify the EAP type (PEAP), but you must also configure a Radius proxy installation file, and then install the Radius proxy to your designated server.
This dialog box has two pages:
As the final step in setting up LANDesk 802.1X NAC support, you must deploy the 802.1X agent to target devices.
This enables compliance scanning and allows the managed devices to be authenticated and either allowed access to the network, or quarantined and remediated.
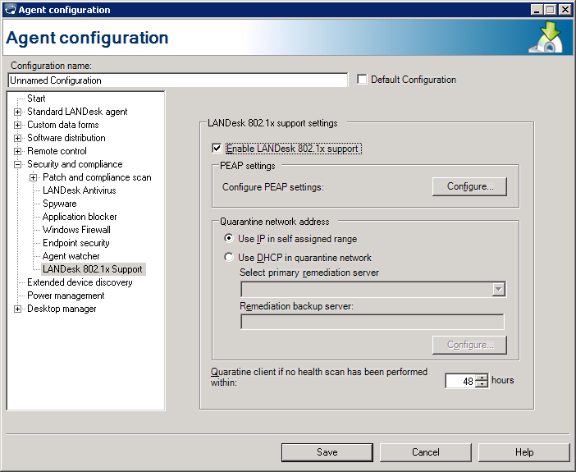
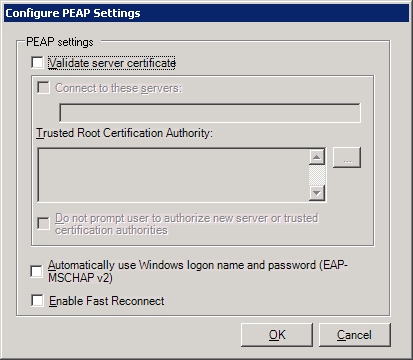
You can now deploy the agent configuration to target devices that you want to use LANDesk 802.1X NAC, and then create compliance scan tasks that scan 802.1X enabled devices for compliance with your security policy.
Network Access Control runs a compliance security scan that determines the device posture or health status according to the criteria defined by your custom security policy.
The compliance scan is performed by a Compliance scan task using Compliance settings with the Enforce 802.1X supported scan option enabled on the Compliance page.
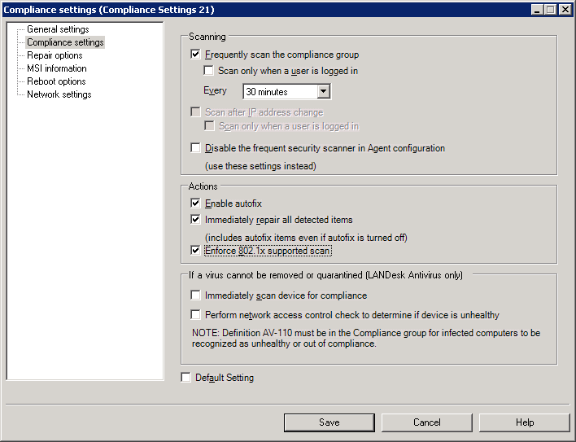
Use the Patch and Compliance tool (Tools > Security > Patch and Compliance) to create compliance security scans. For step-by-step instructions, see Creating security and compliance scan tasks.
NOTE: Compliance
security scans
With the Patch and Compliance tool you can create and configure a
compliance-specific security scan, which checks target devices for
compliance with your customized security policy. A compliance scan
is based on the contents of the Compliance group and can be run as
a scheduled task or as a policy. For information on updating
compliance security rules and policies and republishing NAC
settings, see Managing 802.1X NAC compliance
security.
LANDesk 802.1X NAC requires a switch and router in order to perform authentication and compliance.
Because switch and router hardware is unique to each network environment, providing specific instructions here for every type of hardware is not practical. However, as a general guideline when configuring your switch and router for LANDesk 802.1X NAC, make sure they meet the functionality and topology requirements described in those sections above. For information, see Understanding the 802.1X NAC components and process and Network topology and design considerations.
Also, you can go to the LANDesk Support site for switch and router configuration recommendations and sample configuration files.
The LANDesk User Community has user forums and best known methods for many LANDesk products and technologies. To access this valuable resource, go to: http://community.landesk.com
When a managed device configured with LANDesk 802.1X NAC attempts to connect to the network, the following process occurs:
If the scanned device is healthy it is granted access to the corporate network.
OR
If the scanned device is unhealthy it is placed in the quarantine network where it can be remediated (via the Remediation shortcut on the device desktop) and scanned again in order to gain access to the corporate network.
For a more detailed description of the authentication and compliance process workflow and how the different components interact, see Understanding the 802.1X NAC components and process.
NOTE: Manually
resetting 802.1X authentication at the end user device
If authentication fails even though you're confident the correct
login credentials have been entered, you can manually reset the
local network card to force another authentication attempt. On the
managed device, click Start > LANDesk > 802.1X
reset.
When you run the 802.1X reset option, make sure you first close any
open Windows pop-up dialogs, otherwise the login dialog won't
display. If the login dialog goes away too quickly, it is most
likely caused by the LINK-3-UPDOWN state timing out; simply try the
802.1X reset feature again.
This section contains information about some possible problems you might encounter with LANDesk 802.1X NAC, and how to address them.
Scheduled compliance security scan task returns "lost
connection" status
If a scheduled 802.1X compliance security scan task returns a
status that indicates the target device has "lost connection" or
that the "task failed" it might be because the task status was sent
to the core server while the machine was being restarted. If you
see this status, you can check the target device to verify whether
it was quarantined or not.
With a Huawei switch, multiple 802.1X login prompts
display
When using a Layer 2 Huawei switch (H3C S3900 Series), if a device
displays more than one 802.1X login prompt and the end user cancels
or closes one of them without entering the correct credentials, the
802.1X authentication process is canceled. In this case, users must
enter the correct credentials in each login prompt. If the
authentication is canceled, use the 802.1x reset menu option to
restart the authentication process.
With a Windows XP SP2 device, initial authentication fails
after remediation
If you remediate an unhealthy end user device that is running
Windows XP SP2 and the subsequent authentication attempt fails, you
can use the 802.1X reset menu option to restart the authentication
process and successfully access the corporate network.
If the Radius server is not available, the device fails to
authenticate
In a situation where the 802.1X Radius server is not available to
communicate with the LTA EAP agent on an end user device, the
device is placed in the quarantine network but it doesn't have the
correct configuration, so it can't be remediated and can't
authenticate. You must wait until the Radius server is available,
and then use the 802.1X reset menu option at the device to restart
the authentication process.
802.1X is designed to work on desktop platforms
only
802.1X is not supported on server platforms.