MBSA Management Pack
Microsoft offers Microsoft Baseline Security Analyzer as a way to diagnose the security of servers and workstations. As such, the MBSA MP can be used to schedule agents to scan themselves, diagnosing and providing information on potential vulnerabilities.
The MBSA management pack includes scripts to download MSSecure.cab, ensuring that the latest security information is available. Through a response new to MOM 2005 called File Transfer, this MSSecure.cab can be updated on every agent.
| Note |
All File Transfer responses are issued under the context of LocalSystem (Windows 2000 or Windows 2003) or the Network Service account (Windows 2003 only), despite what the Agent Action Account is running under. |
Coupling this management pack with SMS, an administrator can not only keep their environment patched through SMS but can also be notified if a server is missing a critical patch.
Installation
The Microsoft Baseline Security Analyzer management pack consists of the following files:
-
MicrosoftBaselineSecurityAnalyzer.akm
-
MicrosoftBaselineSecurityAnalyzerReports.xml
-
MBSA MP Guide.doc
As of this writing, the latest version number is 05.0.3100.0000. After downloading the management pack, extract the contents to a common location, and follow the steps in Chapter 8 to import the management pack. After importing the management pack, check the version number against the version number stated in the Management Pack and Product Connector Catalog.
More detail can be found in the MBSA MP Guide.doc, which comes with the management pack. This document can also be found online at http://www.microsoft.com/technet/prodtechnol/mom/mom2005/library/.mspx.
Configuration
The MBSA MP requires that you set up a File Transfer server as part of the configuration. Without this, the agents are not able to retrieve the necessary MSSecure.cab file. This requires setting up some components of IIS. After these prerequisites are completed, the MBSA management pack can be configured. Unlike most management packs, this requires a fairly extensive amount of configuration to get started.
Completing the Prerequisites
During the course of the installations of this book, every completed installation has required IIS. Because of this, you could select any one of these servers to fulfill the requirement of utilizing an IIS server. However, this server must meet some other requirements as well:
-
Internet access to download MSSecure.cab from Microsoft (unless run in manual mode)
-
MOM agent to run scripts in MBSA MP
Often, the same SMS computer performing the Sync Host task can be utilized to perform a sync for this MP as well (installing IIS if necessary). If the MSSecure.cab sync process is run in manual mode, the administrator must pull down MSSecure.cab and place it into the correct location to propagate to the MOM agents. The benefit to this configuration is that Internet access from the File Transfer server is not required.
If the MSSecure.cab synchronization will not be automated, disable the rule "Download Mssecure.cab from http://www.microsoft.com" at Baseline Security Analyzer 1.2/File Transfer Server. Otherwise, MOM generates unnecessary alerts.
Configure the File Transfer Server
Once a server with IIS is identified for use, deploy the agent to the server if it is not yet a MOM agent. Once completed, create a virtual directory for holding the MSSecure.cab file by following these steps:
-
Connect to the server to be used to host the virtual directory.
-
Drill down to the server name, expand Web Sites, and select Default Web Site.
-
On the Default Web Site, right-click. From the extended menu, select New
 Virtual Directory. This launches the
Virtual Directory Creation Wizard. Click Next to begin.
Virtual Directory. This launches the
Virtual Directory Creation Wizard. Click Next to begin. -
When prompted for the Alias name, type MBSA. Click Next.
-
The Agent installation creates a path on every agent in the directory of \Program Files\Microsoft Operations Manager 2005\Downloaded Files\<Management Group Name>. Supply this for the path. Click Next.
-
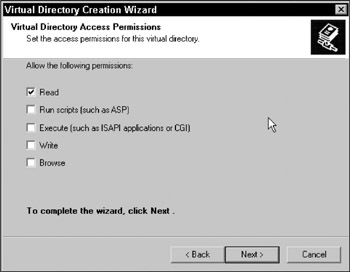
At the Virtual Directory Access Permissions window, make sure only Read is checked, as illustrated in Figure 10-1. Click Next.
-
Click Finish at the last window.
Now with the virtual directory created, grant access to the Internet Guest Account. Remember that at this point, the only granted permissions are "Read."
-
Navigate to the directory used in Step 6 from the preceding list.
-
View the properties of the <Management Group Name> directory.
-
Choose the Security tab and click Add.
-
Under Select this object type, you should see the Users, Groups, or Built-in security principals option. If not, select Object Types and choose Users at a minimum.
-
For From this location, click the Locations option. At the top of the dialog box, the File Transfer server name should be listed. Select the server name and click OK.
-
In the "Enter the object names to select" section, type IUSR_<File Transfer server name> and select Check Names. When the object is found, it should resolve the name. Click OK to continue.
Note IUSR_<File Transfer server name> should be the name of the computer. If the computer name is FTPServer , for example, the account name would look like IUSR_FTPServer.
-
By default, the Internet Guest Account is granted the following permissions:
-
Read & Execute
-
List Folder Contents
-
Read
-
-
Remove or add any rights necessary to match the permissions listed above. Click OK to complete.
Configure MOM Global Settings Web Address
The following steps are required to configure the MOM Global Settings Web Console Address:
-
In the Administrator Console, drill down to Administration/Global Settings.
-
In the Global Setting Type column, open the Web Addresses properties.
-
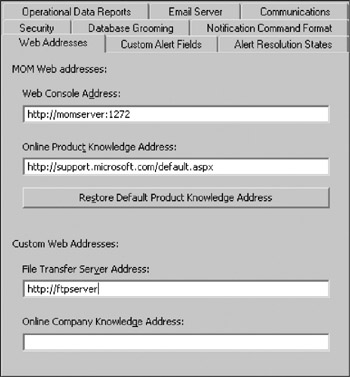
In the Custom Web Addresses section, locate the File Transfer Server Address text box. Type in the address as http://www.filetransferservername. (Refer to Figure 10-2.)
Configure the MBSA Management Pack
The following steps are required to configure the MBSA Management Pack:
-
In the Administrator Console, navigate to Management Packs/Computer Groups.
-
Select the Computer Group name "MBSA File Transfer Server." Right-click the Computer Group and select Properties.
-
There is no formula-or search-based membership in this Computer Group. Associate the File Transfer server to the Computer Group by selecting the Included Computers tab. Add in the File Transfer server and click OK.
Configure the MOM Agents
In order for MOM agents to pull down MSSecure.cab from the File Transfer server, the BITS service needs to be configured. The good news is that if you've deployed SMS 2003 Advanced Clients, the BITS service has already been configured by the SMS client setup.
-
If the File Transfer server is a Windows 2000 Server, BITS does not need to be configured. The MOM agent has the necessary rights to launch the service when required.
-
If the File Transfer server is Windows Server 2003, BITS must be configured to a startup type of Manual or Automatic. In addition, the service must be started.
By default, the rule Run vulnerability and security patch scan is disabled. Because this is probably why you're installing this management pack, enable this rule so that the MOM agents will scan for vulnerabilities with MBSA. This rule is located under Management Packs/Rule Groups/Microsoft Baseline Securitys Analyzer/Baseline Security Analyzer 1.2/MOM Agent.
Components
The MBSA management pack does not use any attributes as part of formulas to determine membership in Computer Groups. The only Computer Group available by this MP, MBSA File Transfer Server, uses "Included Computer" membership (refer to the section "Configure the File Transfer Server"). All other Agent to Rule Group associations are based on the membership for MOM agents. This MP is designed to run on all MOM agents.
No new Notification Groups are created by this management pack. By default, there are no alert rules for any of the alerts generated by this MP. Only one rule runs with a notification response, which generates an alert for the MOM administrator. This rule is called "Download Directory Creation Wizard" and is located under the MOM agent rules of this management pack.
| Important |
The MOM agent rules under this management pack execute for all MOM agents. This means all of your agents will run the rules under this management pack. |
Scripts
The Microsoft Baseline Security Analyzer management pack requires a few scripts to handle pulling down MSSecure.cab from Microsoft, executing the MBSA installations, and running MBSA scans. The following sections provide a description of the scripts included followed by a table including the script parameter names, descriptions, and default values. The goal is to enable the reader to better understand how these scripts work and support managing MBSA.
MBSA Install and Run
The MBSA Install and Run script installs Microsoft Baseline Security Analyzer if it is not detected on the MOM agent. The script also scans the agent for patches and vulnerabilities.
|
Name |
Description |
Value |
|---|---|---|
|
HistoryPatchScanCommand |
Patch scan with history execution command parameters |
“%programfiles%\Microsoft Base line Security Analyzer\mbsacli.exe” -hf -sms -x “%program-files%\Microsoft Baseline Security Analyzer\MSSecure.cab” -f “%userprofile%\SecurityScans\ MomHPScan.xml” -Unicode -nvc -history 1 |
|
MBSAProductGuid |
GUID for MBSA |
{} |
|
MBSASetupFile |
File name for MBSA |
MBSASetup.msi |
|
PatchScanCommand |
Patch scan execution command parameters |
“%programfiles%\Microsoft Base-line Security Analyzer\mbsacli.exe” -hf -sms -x “%program-files%\Microsoft Baseline Security Analyzer\MSSecure.cab” -f “%userprofile%\SecurityScans\ MomPScan. xml” -Unicode -nvc |
|
VulnerabilityScanCommand |
Vulnerability scan execution command parameters |
“%programfiles%\Microsoft Base-line Security Analyzer\mbsacli ⋅exe” -n Updates -o MomVScanNew -nvc |
Tasks
The following table lists the available tasks in this management pack. It also states the context that the task runs in.
|
Task |
Context |
|---|---|
|
Download mssecure.cab from File Transfer Server |
Agent |
|
Download mssecure.cab from http://www.microsoft.com |
Agent |
|
Run MBSA Scan |
Agent |
If the tasks execute in the context of the agent, LocalSystem provides all necessary permissions. However, if the agent runs in least privilege configurations, it may require additional permissions to execute some of the tasks. All console tasks are executed under the permission of the user using the Operator Console. If the user doesn't ordinarily have the rights to execute the task, running the task will fail.