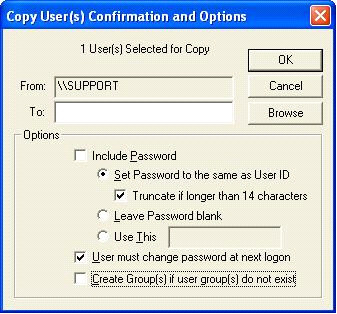
DNTU no longer supports the transfer of passwords from one machine to another when copying users. Ever since Microsoft introduced the SysKey hotfix (128-bit encryption, somewhere around NT SP4) the password is no longer easily accessible. An alternative method would be to set the password the same as UserID and have the user change their password during the next logon.

Here is what Microsoft has to say about SysKey:
What's Syskey?
Syskey is a feature first introduced in Windows NT® 4.0 (and
provided as part of Windows 2000) that makes it more difficult for
an attacker to compromise passwords on a Windows NT machine.
In Windows NT and Windows 2000, passwords are stored in the Security Account Manager (SAM) database. The password values themselves aren't stored in the SAM - instead, the hashed values of the passwords are stored there. If an attacker could obtain a copy of the SAM through some means, he could conduct a brute-force attack, in which he would generate the hash of every possible password and compare each to the hashes in the SAM database. When he found a match, he would know the password for the account.
Syskey thwarts this attack by encrypting the SAM database using strong encryption. Even if an attacker did manage to obtain a copy of the Syskey-protected SAM, he would first need to conduct a brute-force attack to determine the Syskey, then conduct a brute-force attack against the hashes themselves. This dramatically increases the work factor associated with the attack, to the point where it's considered to be computationally infeasible.
What's EFS?
The Encrypting File System (EFS) is a feature in Windows 2000 that
provides cryptographic protection for files on the machine. EFS was
designed to thwart an attack in which an attacker who has physical
control of a Windows 2000 machine would boot the stolen machine
using an operating system that doesn't respect the Windows 2000
access controls, then copy the files. EFS blocks this attack by
encrypting user-specified files. If an attacker stole these
encrypted files, he would need to conduct a separate brute-force
cryptographic attack against each file in order to read its
contents.
A feature of EFS that plays a central role in the discussion here is the EFS Recovery Agent. A Recovery Agent is a user who is authorized to decrypt files belonging to other users. The chief use of this feature is to allow files to be decrypted in the event that the original owner loses the key. Whenever a file is encrypted by EFS, EFS also creates a copy of the key that is accessible by the Recovery Agent. By default, administrators are Recovery Agents - the local administrator in the case of a local user, and the domain administrator in the case of a domain user. However, the list of Recovery Agents can be customized via security policy.
You can also refer to the following Microsoft Knowledge Base article for more information:
Windows NT System Key Permits
Strong Encryption of the SAM
http://support.microsoft.com/default.aspx?scid=KB;EN-US;Q143475&