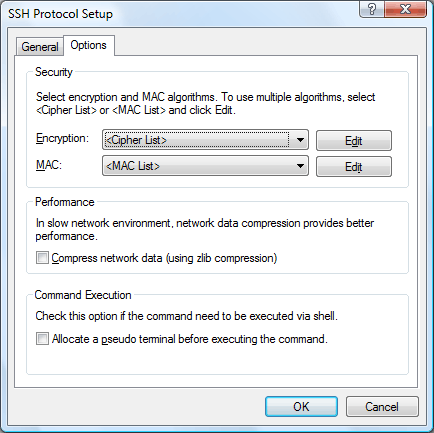
In the Options tab, you can configure security, performance and pseudo terminal options.

Encryption algorithms are used to encrypt and decrypt network traffics. You can select a preferred encryption algorithm in the list. When you select the Cipher List, multiple algorithms are tried in order of appearance in the list. To edit the Cipher List, click Edit.
MACMAC(Message Authentication Code) ensures data integrity and it provides increased security of SSH2 protocol over SSH1. You can select a preferred MAC algorithm in the list. When you select the MAC List, multiple algorithms are tried in order of appearance in the list. To edit the MAC List, click Edit.
Compress network dataSelect this check box to compress all data traffic with the zlib algorithm. Compression will provide better performance in a slow network environment.
Allocate a pseudo terminal before executing the commandSelect this check box when you want to allocate a pseudo terminal on the remote host and then run a command on the pseudo terminal. A pseudo terminal is required for some X applications and it ensures that shell environment variables are configured correctly as a normal logon.