 Important: Important: |
|---|
| This is retired content. This content is outdated and is no longer being maintained. It is provided as a courtesy for individuals who are still using these technologies. This content may contain URLs that were valid when originally published, but now link to sites or pages that no longer exist. |
The CM_ProxyEntriesConfiguration Service Provider configures proxy connections on the device.
 Note: Note: |
|---|
| This Configuration Service Provider is managed over the OMA Client Provisioning protocol. To provision devices using the OMA DM protocol, use the PROXY Configuration Service Providerinstead. Access to this Configuration Service Provider is determined by security roles. Because OEMs and mobile operators can selectively disallow access, ask them about the availability of this Configuration Service Provider. For more information about roles, see Security Rolesand Default Roles for Configuration Service Providers. |
The nocharacteristictag will work on the top two levels to delete all, or specific, entries.
The following table shows the default settings. The default security role maps to each subnode unless specific permission is granted to the subnode.
|
Permissions |
Read/Write |
|
Roles allowed to query and update setting |
Manager AuthenticatedUser |
The following image shows the Configuration Service Provider in tree format as used by OMA Client Provisioning.
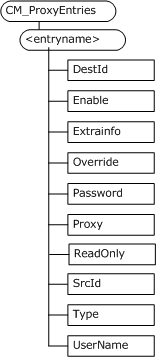
 Characteristics
Characteristics
- <entryname>
-
Specifies settings for the <entryname>parameter that sets the name of the connection. Settings under this characteristic specify parameters for this proxy connection.
 Parameters
Parameters
- Enable
-
This parameter can be used in the <entryname>characteristic to enable or disable a connection entry without removing it from the system. Permitted values are 0 for OFF or 1 for ON.
The following table shows the default settings.
Permissions
Read/Write
Data type
Boolean
Label
Enable
Roles allowed to query and update setting
Manager
AuthenticatedUser
- Extrainfo
-
Used in the <entryname> characteristic to store additional information that does not fit appropriately into any of the other proxy fields. Typically, this parameter is used to store additional WAP proxy information.
The following table shows the default settings.
Permissions
Read/Write
Roles allowed to query and update setting
Manager
AuthenticatedUser
- DestId
-
Used in the <entryname> characteristic as a GUID that represents the unique ID of the network to which this entry connects. See the Connmgr.h header for predefined GUID values IID_DestNet*.
Typically, a proxy connection connects from a private network to the Internet, so the value of DestId would be that of IID_DestNetInternet, which is "{436EF144-B4FB-4863-A041-8F905A62C572}."
The following table shows the default settings.
Permissions
Read/Write
Data type
String
Label
Connects to
Roles allowed to query and update setting
Manager
AuthenticatedUser
- Override
-
Reserved for future use.
- Password
-
Used in the <entryname> characteristic to specify the password of the proxy entry, if one exists. Passwords are only required for WAP and SOCKS proxies and are not used for HTTP proxies. Queries of this field return a string composed of asterisks (*).
When setting the password, passing in the same string causes the new password to be ignored and does not change the existing password.
The following table shows the default settings.
Permissions
Read/Write
Data type
String
Label
Password:
Semantic type
alphanumeric-password
Roles allowed to query and update setting
Manager
AuthenticatedUser
- Proxy
-
Used in the <entryname> characteristic to specify the name and port number of the proxy server. For HTTP proxies, the value of this parameter uses the <name>:<port> format, for example, myproxy:80.
The following table shows the default settings.
Permissions
Read/Write
Data type
String
Label
Proxy (name:port):
Semantic type
url
Roles allowed to query and update setting
Manager
AuthenticatedUser
- ReadOnly
-
This parameter is used in the <entryname>characteristic and determines whether users are able to modify proxy settings. Permitted values are 0 for false and 1 for true. If the value is set to 1, users will be able to view, but not change, the proxy settings on the device.
The following table shows the default settings.
Permissions
Read/Write
Data type
Boolean
Roles allowed to query and update setting
Manager
Operator TPS
- SrcId
-
Used in the <entryname> characteristic as a GUID that represents the unique ID of the network from which this entry connects. See the Connmgr.h header for predefined GUID values IID_DestNet*.
The following table shows the default settings.
Permissions
Read/Write
Data type
String
Label
Connects from:
Roles allowed to query and update setting
Manager
AuthenticatedUser
- Type
-
Used in the <entryname> characteristic to specify the type of the proxy entry. Possible values are:
- 0 for null proxies
- 1 for HTTP proxies
- 2 for WAP proxies
- 4 for SOCKS4 proxies
- 5 for SOCKS5 proxies
The value of 0 is reserved to denote a null proxy. This value can be used to allow Connection Manager to treat one network as a superset of another network by creating a null proxy from one network to the other.
The following table shows the default settings.
Permissions
Read/Write
Data type
String
Roles allowed to query and update setting
Manager
AuthenticatedUser
- 0 for null proxies
- UserName
-
If a proxy entry exists, this parameter is used in the <entryname>characteristic to specify the username of the proxy entry.
The following table shows the default settings.
Permissions
Read/Write
Roles allowed to query and update setting
Manager
AuthenticatedUser
 Microsoft Custom Elements
Microsoft Custom Elements
The following table shows the Microsoft custom elements that this Configuration Service Provider supports for OMA Client Provisioning.
| Elements | Available |
|---|---|
|
parm-query |
Yes |
|
noparm |
No |
|
nocharacteristic |
Yes Top-level: Yes |
|
characteristic-query |
Yes Recursive query: Yes Top level query: Yes |
Use these elements to build standard OMA Client Provisioning configuration XML. For information about specific elements, see MSPROV DTD Elements. For general examples of how to use the Microsoft custom elements, see OMA Client Provisioning XML File Examples.
For information about OMA Client Provisioning, see OMA Client Provisioning Files.







 See Also
See Also