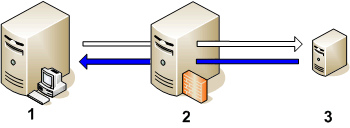
You can redirect connections from management servers and nodes that are on different networks through a proxy. The figure below shows connections between a management server and node through a proxy as follows:

You can also redirect communication through proxies in more complex environments as follows:
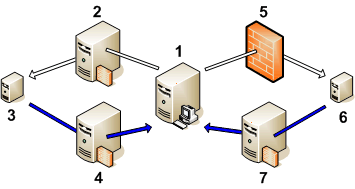
The figure below shows connections between a management server and nodes through multiple proxies as follows:
You redirect outbound HTTPS communication through proxies by
setting the PROXY parameter in the
bbc.http name space on the management servers
and nodes. You can configure this parameter in the following
ways:
ovconfchg or ovconfpar at a
command prompt.The value of the PROXY parameter can contain one or more proxy definitions. Specify each proxy in the following format:
<proxy_hostname>:<proxy_port>+(<included
hosts>)-(<excluded hosts>)
Replace <included_hosts> with a
comma-separated list of hostnames or IP addresses to which the
proxy enables communication. Replace <excluded
hosts> with a comma-separated list of hostnames or IP
addresses to which the proxy cannot connect. Asterisks (*) are wild
cards in hostnames and IP addresses. Both
<included_hosts> and
<excluded hosts> are optional.
To specify multiple proxies, separate each proxy with a semicolon (;). The first suitable proxy in the list takes precedence.
To configure a node to use proxy1.example.com port
8080 for all outbound connections, you would use the
following value:
proxy1.example.com:8080
To configure a management server to use
proxy2.example.com:8080 to connect to any host with a
hostname that matches *.example.com or
*example.org except hosts with an IP address in the
range 192.168.0.0 to 192.168.255.255, you would use the following
value:
proxy2.example.com:8080+(*.example.com,*.example.org)-(192.168.*.*)
To extend the above example to use
proxy3.example.com to connect to
backup.example.com only, you would use the following
value:
proxy3.example.com:8080+(backup.example.com);
proxy2.example.com:8080+(*.example.com,*.example.org)-(192.168.*.*)
In the above example,
proxy3.example.com:8080+(backup.example.com) must be
first, because the include list for proxy2.example.com
contains *.example.com.
ovconfchgexport
PATH=/opt/OV/bin:$PATH and then press Enter.export
PATH=/usr/lpp/OV/bin:$PATH and then press
Enter.export
PATH=/usr/opt/OV/bin:$PATH and then press
Enter.Specify the proxies that the node should use. You can specify different proxies to use depending on the host that the agent wants to connect to. Type the following command:
ovconfchg -ns bbc.http -set PROXY
<proxy>
![]() NOTE:
NOTE:
When you use the command ovconfchg on a management
server that runs in a cluster, add the parameter -ovrg
server.
Related Topics: